Issue User Certificates for Azure AD/Entra AD Certificate Based Authentication Using OpenSSL
If you use OpenSSL to provide a CA and want to test certificate based authentication for Azure AD, use this guide to get a M365 compliant certificate issued.

This article assumes that you have an active OpenSSL Certificate Authority setup and have configured Azure AD to trust certificates issued by this CA. For more information on Azure AD & Certificate Authentication, please see: https://learn.microsoft.com/en-us/azure/active-directory/authentication/how-to-certificate-based-authentication
The following guide explains how to issue OpenSSL certificates that allow user authentication in line with Microsoft's UPN requirements.
Example CSR Configuration File
Remember to change %replace% with the relevant attributes for your CA and %replace-with-upn% with the UPN of the user being issued the certificate, as it's configured in Azure AD.
[ req ]
default_md = sha256
prompt = no
req_extensions = v3_req
distinguished_name = req_distinguished_name
[ req_distinguished_name ]
commonName = %replace-with-upn%
countryName = GB
stateOrProvinceName = %replace%
localityName = %replace%
organizationName = %replace%
organizationalUnitName = User Certificates
[ v3_req ]
keyUsage=critical,digitalSignature,keyEncipherment
extendedKeyUsage=critical,serverAuth,clientAuth,codeSigning,emailProtection
subjectAltName = @alt_names
[ alt_names ]
otherName.0 = 1.3.6.1.4.1.311.20.2.3;UTF8:%replace-with-upn%
otherName.1 = msUPN;UTF8:%replace-with-upn%
email.0 = %replace-with-upn%Issue the Certificate
- Generate a Private Key: `openssl genpkey -outform PEM -algorithm RSA -pkeyopt rsa_keygen_bits:2048 -out priv.key`
- Generate the CSR based on the configuration above:
openssl req -new -nodes -key priv.key -config csrconfig.txt -nameopt utf8 -utf8 -out csr.pem - Sign the CSR:
openssl ca -days 3650 -in csr.pem -out certificate.crt -extfile csrconfig.txt -extensions v3_req -config /path/to/ca/openssl.conf - Create a PFX to allow the Certificate and the Key to be imported into user accounts:
openssl pkcs12 -inkey priv.key -in certificate.crt -export -out export.pfx
Install the Certificate
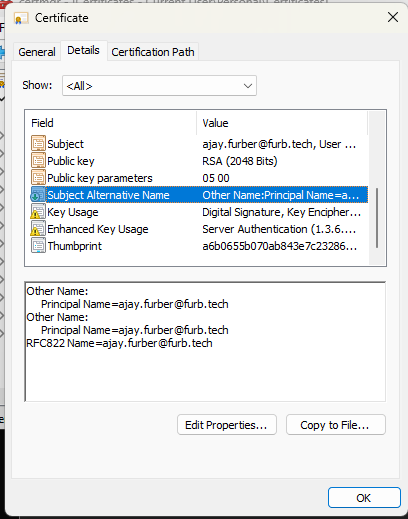
Install the PFX into the relevant client devices to allow certificate based authentication. These should be installed under the relevant user account into the "Personal" certificate store. On Windows you can view the certificate in mmc.exe to check the UPN has been included similar to the below: